THM Write-Up: Windows Event Logs
This is my write-up for working through the Windows Event Log room —
https://tryhackme.com/room/windowseventlogs
Thanks to the THM team for creating this platform and providing excellent learning material for us students in cyber security :)
Before starting, I highly recommend working through the room on your own! This guide provides the answers, followed by an explanation on how the solution was found.
1 — Event Logs
These records document activity that occurs in a system and can be used for various things, from diagnosing problems to conducting review of an incident. Log entries help investigators see a timeline of events to help determine what occurred on a system or device. For those seeking roles in a SOC or other blue team security role, one major core responsibility is working with SIEMs and review logs to respond to an incident accordingly.
Before starting the room, launch the room’s machine. It will deploy an instance of Windows, so no remoting is necessary from the attack box at this time.
Let’s begin…
2 — Event Viewer (GUI-based application)
For reference, it is important to note that there are three ways to access event logs, which will be covered in Task 2–4. For now, we are reviewing the GUI method (accessed via right-clicking on Start and selecting Event Viewer). To answer the questions, we will need to select the proper log:
Applications and Services Logs > Microsoft > Windows > Powershell > Operational
What is the Event ID for the first event?
- Answer: 40961
The first log may be the most recent event listed. By clicking on Date and Time, the logs can be sorted from the oldest to most recent and vice-versa. Once sorting, we can find the oldest log to occur at 12/21/2020 6:56:02 AM, with the event ID.
Filter on Event ID 4104. What was the 2nd command executed in the PowerShell session?
- Answer: whoami
Select “Filter Current Log…” from the right-hand menu. Add the desired ID to the field, then click OK.
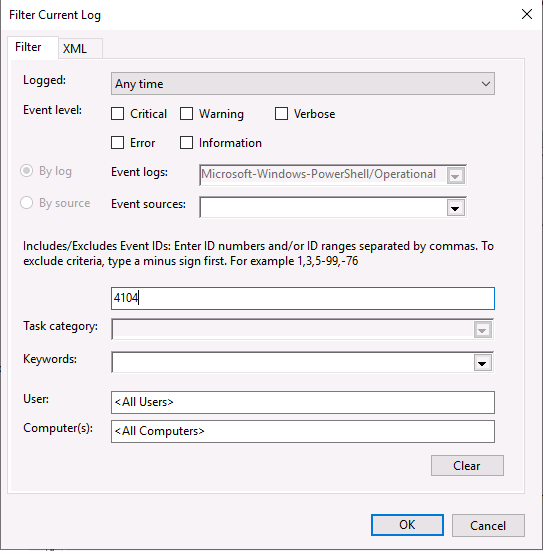
The logs should all have the same event ID requested. Clicking on the second log, we can take a look under the General section and see that whoami was run:

What is the Task Category for Event ID 4104?
- Answer: Execute a Remote Command
Still viewing the same event from the previous question, we can see additional details on this event below:

What is the Task Category for Event ID 800?
- Answer: Pipeline Execution Details
On the left-hand side, navigate to Applications and Service Logs > Windows PowerShell (standalone log):

Once clicking on the log entry, we can see the events listed with Event ID 800. Similar to the previous question, review the Task Category section to find the answer.
3 — wevtutil.exe (command-line tool)
The “Windows EVenT UTILity” tool allows for viewing event log information via the command prompt instead. Open the Command Prompt (I personally recommend opening Windows PowerShell prompt instead) and type wevtutil.exe /? to view more information on what can be used in combination with the tool for more efficient use. After review, we can move on to answering the questions…
How many log names are in the machine?
- Answer: wevtutil.exe el | Measure-Object
Recalling reviewing the commands via the help guide. The best command would be ‘wevtutil.exe el’ to list the log names, BUT this command returns a list of all the logs and we just need the count. Piping this command with the PowerShell module Measure-Object is recommended per the Hint provided (note: this must be run via Windows PowerShell, not Command Prompt).

What is the definition for the query-events command?
- Answer: Read events from an event log, log file or using structured query.
The commands in the help section can be reviewed in more detail by running a similar command: wevtutil.exe <command> /?
In this case, we can run wevtutil.exe qe /? to find our answer:

What option would you use to provide a path to a log file?
- Answer: /lf:true
Still working through the wevtutil.exe qe /? guide, look under Options. There are a couple of ways to write this command, but the answer is looking for use of /lf instead of /logfile.

What is the VALUE for /q?
- Answer: Xpath query
Again, still looking at the guide from the previous question, we see the answer listed under /{q | query}:VALUE.
The questions below are based on this command:
wevtutil qe Application /c:3 /rd:true /f:text
- No answer needed, just enter the command in the prompt.
What is this command doing, anyway? Recall the guide we have been looking into:
wevtutil qe Application — We are looking to read events from the log Application via structured query.
/c:3 — maximum number of events to read is set to the count of 3
/rd:true — we are asking for the events to be listed with the most recent first
/f:text — this is telling the command to return the format in text instead of the default (XML).
What is the log name?
- Answer: Application
This can be determined from the first part of the command, recalling the previous explanation above: wevtutil qe Application — We are looking to read events from the log Application via structured query.
What is the /rd option for?
- Answer: Event read direction
The answer can be found under wevtutil.exe qe /?

What is the /c option for?
- Answer: Maximum number of events to read
Similar to the previous question, refer to wevtutil.exe qe /?

4 — Get-WinEvent (PowerShell cmdlet)
Another way we can view the event logs is via this cmdlet, which must be run via PowerShell. There is a lot of information on its use provided by THM and Microsoft, so take the time to read about it and check out the help guides.
Execute the command from Example 1 (as is). What are the names of the logs related to OpenSSH?
- Answer: OpenSSH/Admin,OpenSSH/Operational
Remember, this is referring to the example from the online documentation! The command to run is: Get-WinEvent -ListLog *
It outputs a long list with the wildcard, so thankfully the answers are viewable at the bottom.
Execute the commands from Example 7.
- Answer: Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager/Debug
Run the following command — Get-WinEvent -ListProvider *PowerShell*
The answer will be located under LogLinks.
Execute the command from Example 8. Use Microsoft-Windows-PowerShell as the log provider. How many event ids are displayed for this event provider?
- Answer: 192
The ideal command needed is — (Get-WinEvent -ListProvider Microsoft-Windows-PowerShell).Events | Format-Table Id, Description
This command will output all related information with the ID and description, but we are just looking for the count. Recall the Measure-Object cmdlet.

How do you specify the number of events to display?
- Answer: -MaxEvents
This can be confirmed via the online documentation.
5 — XPath Queries
This section covers XPath (XML Path Language) filtered events, and how they can be constructed from Details via Event Viewer.
Based on the docs.microsoft.com, an XPath event query starts with ‘*’ or ‘Event’.
Great, now to figure out how to construct a query. Conveniently, the shortcut to Event Viewer is provided in the VM via the bar below. Once opened:
- Navigate to Applications and Service Logs > Windows Logs > Application.
- Clicking on any of these logs, we can view the general information.
- Select Details > XML View to see the ‘<Event xmlns=…’ description for an idea.
The recommended command is —
Get-WinEvent -LogName Application -FilterXPath ‘*/System/’
We see that in the XML View panel, there are multiple categories we can call on to add to our command, substituting the values with the ones we are looking for.

Multiple queries can be added together, just make sure they are contained within the single quotations. Write them as you would a single command, but spaced with the keyword “and” between both queries.
To search for more granular information and complete the following questions, we will need to understand how to make some modifications to the query, as seen in the THM example below:

Using Get-WinEvent and XPath, what is the query to find WLMS events with a System Time of 2020–12–15T01:09:08.940277500Z?
- Answer**: Get-WinEvent -LogName Application -FilterXPath ‘*/System/TimeCreated [@SystemTime=”2020–12–15T01:09:08.940277500Z”] and */System/Provider[@Name=”WLMS”]’
Using XML View, we can see that under <System> is <TimeCreated SystemTime=”…”>. Some of these may involve trial and error, so be sure to take the time to read the formatting for the queries. This query needed to be flipped to be accepted by THM, but the order should not impact the search in this case.
Using Get-WinEvent and XPath, what is the query to find a user named Sam with an Logon Event ID of 4720?
- Answer: Get-WinEvent -LogName Security -FilterXPath ‘*/EventData/Data[@Name=”TargetUsername”]=”Sam” and */System/EventID=4720’
Change LogName to look at the Security log for user logon events as this is where they are stored.
Based on the previous query, how many results are returned?
- Answer: 2
Run the exact command from the previous question via PowerShell. This command will also get you the answer for the remaining questions.
Based on the output from the question #2, what is Message?
- Answer: A user account was created
Still working with Sam as the user, what time was Event ID 4724 recorded? (MM/DD/YYYY H:MM:SS [AM/PM])
- Answer: 12/17/2020 1:57:14 PM
Run the previous command, but replace with EventID=4724
What is the Provider Name?
- Answer: Microsoft-Windows-Security-Auditing
Unfortunately, XPath queries cannot use wildcards in the search fields (with exception to the beginning part). We can just view the Provider via GUI by revisiting Event Viewer, navigating to Windows Logs > Security > Details > XML View.

6 — Event IDs
Take time to review some of the provided resources, in addition to glancing over this event list, as they are good for foundational knowledge.
No questions for this section.
7 — Putting Theory Into Practice
Get ready to recap and implement some Google-Fu (this skill is essential, I will have a standalone article on this soon), feel free to try other alternatives to finding these answers as well.
Begin by opening ‘merged.evtx’ log, in the Desktop. Take a moment to study what’s going on. These type of obfuscation attacks are commonplace, sometimes even encrypted. You will most likely run into them again at some point in your studies or career so it is important to be able to recognize this as very unusual activity (sometimes legitimate, strangely enough, but *very* rare that it is).
What event ID is to detect a PowerShell downgrade attack?
- Answer: 400
We can determine the Event ID from the following article found via Google.
What is the Date and Time this attack took place? (MM/DD/YYYY H:MM:SS [AM/PM])
- Answer: 12/18/2020 7:50:33 AM
Using Event Viewer, select Filter Current Log and input Event ID = 400. All related activity will be listed, but we need to determine the earliest time of occurrence. However, if you use XPath, you’ll have to perform some command line magic:
Get-WinEvent -Path C:\Users\Administrator\Desktop\merged.evtx -FilterPath ‘*/System/EventID=400’
A Log clear event was recorded. What is the ‘Event Record ID’?
- Answer: 27736
Searching Google again led to finding this action to be listed as Event ID 104. Via Event Viewer, the following details can be confirmed:

What is the name of the computer?
- Answer: PC01.example.corp
What is the name of the first variable within the PowerShell command?
- Answer: $Va5w3n8
Filter Current Log > set Event ID = 4104. Find the first event, then view ScriptBlockText via Details. Recall that PowerShell variables begin with ‘$’.
What is the Date and Time this attack took place? (MM/DD/YYYY H:MM:SS [AM/PM])
- Answer: 8/25/2020 10:09:28 PM
If you’d like to try XPath, run the following command:
Get-WinEvent -Path C:\Users\Administrator\Desktop\merged.evtx -FilterPath ‘*/System/EventID=4104 and */EventData/Data[@Name=”scriptblocktext”]’
What is the Execution Process ID?
- Answer: 6620
Reviewing the same entry in Event Viewer, switch to XML View and scroll down to find this data entry.
What is the Group Security ID of the group she enumerated?
- Answer: S-1–5–32–544
Back to Google search, we find that enumeration involves Event ID 4798 and 4799. Since we are likely looking for the activity affecting a group, filter on 4799 and view the earliest entry. Check Details and it will be the TargetSid.
What is the event ID?
- Answer: 4799
SO MANY LOGS!
…aaand we are all done here now. Hopefully you walked away with a new understanding of Windows Event Log and how it works since it is a great resource for investigations! I recommend revisiting this lab a couple of times and playing with the Event Viewer on your own machines to get the hang of it as well.
